8 Common Types of Cyber Attacks And How To Prevent Them

In 2019, the U.S. government decided to spend $15 billion to prevent Cyber Threats that is 4.1% more than the 2018 budget. The main reason for spending a huge amount is different types of Cyber Attacks that occur randomly.
What is a Cyber Attack?
A Cyberattack is a malicious activity that is performed by an individual or organization intentionally on another individual or organization. The purpose behind such attacks is to breach the information security system and steal or infect necessary data. Usually, Hackers perform some common types of Cyber threats to gain control over a system. Which you can prevent easily if you know about it.

Today we will discuss the top 8 types of Cyber Attacks that execute by hackers. Also, I’m gonna tell you some super important tips to prevent such threats, which come on cybersecurity basics. If you have been a victim of any of that attack before or you want to protect yourself then read it carefully.
8 Common Types of Cyber Attacks
- Phishing
- MitM Attack
- SQL Injection
- DDoS Attack
- Malware
- Social Engineering
- XSS Attack
- Password Attack
Phishing Attack[ps2id id=’1′ target=”/]
Phishing is a kind of Social Engineering that is used to steal some sensitive and important data of a user. This data could be anything like Credit card details, login credentials. Hackers can even install malware on your device by using the Phishing technique. Some attackers use a phishing method to make a fake e-commerce website, where some use it to build fake social media websites.
There’s no doubt that phishing attacks are increasing in large amounts every year. Almost every year at least 15% of people worldwide face this cyber attack.
How Phishing Works?
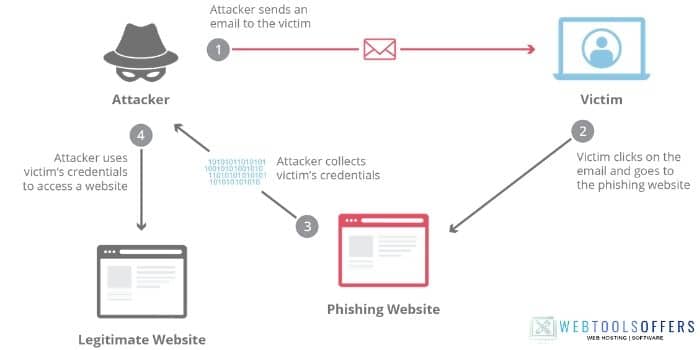
Let’s assume that I’m a hacker and I want to steal the login credential of your Facebook account. The first thing I will do, build a fake web page of Facebook by using HTML and CSS.
Once I made a fake Facebook webpage, the next step to send you the link. I will send you that link by email with the message “An invalid attempt of login happened recently. Secure your account if it wasn’t you.”. But I will be assured that you will get that link from a familiar name. For that, I will make a fake e-mail address to gain your trust.
7 people out of 10, now will open that link to change the password. The victim will land on the fake forget password page where he/she need to insert the current user id and password for the next process. After filling in all info, I will show a fake message of password change successfully.
Now I have your id and password that I can use to steal your data.
Note:- It’s just a scenario that I present of password-stealing but some people send a fake link to view the documents by FB login. Once you enter the login credential, your data will be stored and you will be redirected to the original site.
How to Identify and prevent Phishing Attack?

Identifying a phishing attempt is not very difficult. By focusing on some important elements you can easily protect yourself from these types of Cyber Attacks.
- Never open a link that seems infected. If you are a Gmail user, you may have seen the warning message on spam emails.
- If you received an e-mail in your inbox that looks like from a known person. Then contact the person and ask them about it. Clear your about before filling in your details.
- Almost everyday attackers send emails to people that they have won a huge amount like $10Million on a lottery prize. To claim this they have to fill in their bank details. I suggest you to never run for lottery prize mail because all of them are a fraud. They get your bank details and steal all of your money.
- If you got an SMS of any password change or asking about login information then first open the official link and try to log in. If you don’t find any warning over there means you are safe and it just a phishing attack. You can contact me to help support too.
- Do not shop from any random e-commerce website. Only purchase from that website that is reputed and provide security if you are using your card details.
Man-in-the-Middle Attack (MitM)[ps2id id=’2′ target=”/]
Normally communication happens between a user and the servers to send and request the required data. But when an attacker disturbs the communication and gains control over it then it is known as a Man-in-the-Middle attack.

Once the hackers have control over the device they can see, edit, or even alter the data. Here are the main types of MitM attacks.
- Session Hijacking
- IP spoofing
- Replay
How a Man-in-the-Middle attack occur?
The most common way to get an attack by a MitM attack is either using public wifi or using a malware-infected software/application.
You may be heard before that open networks such as public wifi are very vulnerable. That’s the reason why hackers love those places so much. Even some of the open networks are created by hackers, just to steal the information.
How does it work?
When you connect to an open network, at that moment you are totally vulnerable(if you are not using a VPN or antivirus). Hackers take control over your device and disconnect you from the server and connect themselves in the place of you. To make the server believe that the client is still connected with it, the attacker changes its IP with yours. Now the attacker can easily manipulate or steal all the data from the server.
How to prevent from Man-in-the-Middle attack?

MitM attacks are one of the most dangerous types of cyberattacks, by which a hacker can steal your identity as well as money too. But there are some simple ways to prevent such attacks.
- Try to avoid using public networks like Cafe, Railway Station, or Library.
- Use VPN software to mask or hide your IP address. PureVPN, CyberGhost, VyprVPN are some best VPN software that is affordable too.
- Never install any third-party application on your device.
- If you want to use third-party software then using the best antivirus software helps you to protect from MitM attacks. Kaspersky, Bitdefender, and Heimdal Security are the best options to remove any harmful software from your device.
SQL Injection
[ps2id id=’3′ target=”/]
SQL Injection is also known as Structured Query Language Injection, which is a popular type of cyber attack. In this attack, an attacker inserts malicious code to gain access to database tables. With this method, a hacker can easily view all the data that should not be displayed.
This information can contain login credentials, bank details, and some more private data.
Apart from viewing data, the attacker can edit and delete all the tables of the database.
How hackers perform SQL Injection attacks?
Here is an example of SQL injection that is performed by the attacker on a vulnerable website.
“Select * from users where id=’”+ 1234 +”’;”
With this query, a hacker can view all the data of the users and by modifying or deleting the function he can alter or remove the data. You can also select all the users of a database by replacing the id “‘ or ‘1’ = ‘1’”. Here’s the query that looks like after replacing a single user id.
“Select * from users where id=‘’ or ‘1’ = ‘1’;”
How to protect a website from SQL Injection?
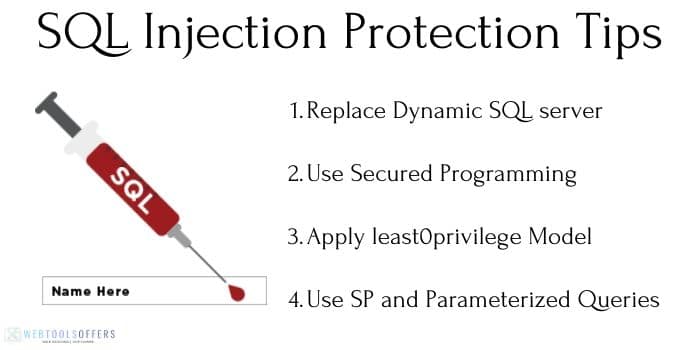
The SQL injection attack is one of the oldest cyberattack tactics that was used by hackers. Still, you can’t neglect security concerns towards this threat. Here are some tips to protect a website from SQL Injection.
- If your website is running on a dynamic SQL server then replace it. Because mostly SQL injection attacks are performed on those websites that have dynamic SQL.
- If your website is developed using the old version of PHP or ASP then replace it with ASP.NET and J2EE. Because the old version is vulnerable to SQL Injections.
- Apply the least0privilege model of permissions to your website database. It will protect your website database from all injection threats.
- Use strongly written store procedures and use parameterized queries into your database to make it more secure.
DDoS Attack
[ps2id id=’4′ target=”/]
Distributed Denial of Service Attack is used by hackers to make a website unavailable for the users. Basically, a DDoS attack targets the system resources and sends a huge amount of traffic or flood on a server that it can’t handle. Result in this, the server consumes all the bandwidth and the website becomes inaccessible.

Why hackers use DDoS attacks
These types of cyberattacks mainly do not give direct benefits to hackers. Here are some reasons why hackers launch a DDoS attack on an individual or organization.
- Mainly a DDoS attack is just a distraction for an organization. It diverts the mind of the organization towards the website, so the hacker can breach the security.
- Sometimes businessman hires hackers to perform such an attack on their competitor’s website. They get money in return for doing this cyber attack.
- Personal rivalry could also a reason why hackers perform DDoS attacks.
How to protect an organization’s website from DDoS attacks?

As we know that most DDoS attacks are performed on a highly reputed individual or organization’s websites and services. It is not too difficult to fight against DDoS attacks to protect your website or server. Here are couples of tips to protect your website/service/servers from these cyber threats.
High Bandwidth
Earlier we discussed, DDoS attacks on website resource that includes bandwidth, which highly needs to run a website smoothly. So, if you want to keep secure your website from DDoS attacks then get more bandwidth for your website. That increases the possibility that your website won’t slow down at the time of such a cyber attack.
Multiple Data Centers
If your server is located on a single data center, then it would be easy for hackers to perform a hacking attempt on your website. Using multiple data centers, which should be located in different countries makes it difficult for hackers to perform DDoS attacks.
Malware
[ps2id id=’6′ target=”/]
Malware is made of two words Malicious Software that is intentionally made by hackers to harm/steal the computers, servers, or complete network data. The internet is full of malware programs. From torrent to email, hackers had spread this in most places.
You definitely also have encountered malware in the spam attachment or a malicious website. Hackers also patch malware with software by the reverse-engineering method. It can be in any form that becomes hard to detect if you are not using a good antivirus.
Here are some different types of malware programs, which made by hackers.
- Ransomware
- Worms
- Macro Viruses
- Trojans
- File infectors
- Logic Bombs
- System infectors
How malware reach your systems?
We already know that hackers spread malware on those places where most people are active daily. Some of these places are Email, file downloading websites, Adult websites, or Torrenting websites.
Let’s take an example of an Email malware attack. An attacker attaches a script, link, or software into the mail and definitely write an attention seeker heading and body. A huge number of attackers send lottery mail or other fake special offers to grab your attention. If any chance you have opened the script or installed the software in your system then the malware will start infected your system.
Malware destruction totally depends on hackers’ skills. Skillful hackers can create powerful malware programs that can destroy the whole network in a few minutes.
How to protect a system from a malware attack?

As we know that malware can be very harmful once it is spread or inserted into your system. But there are also some tips that you can use to protect your devices from being a victim of malware attacks.
- Stay away from spam or suspicious emails because they can contain malware scripts.
- Do not open any malicious website that is not protected by an SSL certificate.
- Don’t make use of the adult website, because most malware scripts are spread over there.
- Always use a VPN while doing torrenting for better security. ( You may use the fastest PureVPN Coupon Code for doing torrenting at a very low cost).
- Replace your free antivirus with a purchased one. The main reason behind this step is free antivirus programs don’t provide full protection against such harmful programs.
Social Engineering
[ps2id id=’7′ target=”/]
Social Engineering is an art that attackers use to gain the trust of the victim. Once the victim becomes familiar and started sharing its personal things like Date of Birth, Mobile No., and family details. Once hackers get all the personal details of the victim then hacking the account becomes easier.
Let’s assume that I’m an attacker and I’ll do social engineering on you. The first motive of mine is to gain trust in yours. For that, I will share my fake personal details and try to become very friendly. In return, I will ask for your personal details like DOB, contact details, family, and many other things. Soon you will feel comfortable with me sharing things and then I will send you a link and tell you to open, which contains malware. You will do the same because of trust and now I’ve control over your device and you don’t have an idea about it. Social Engineering is one of the types of cyber attacks that harm indirectly the victim.
Why Social Engineering is very dangerous?
Social Engineering is a clever move that hackers use when they are unable to directly access your system. First, they won your trust and then ask your personal details that you don’t have to share with unknown people.
Social Engineering is very dangerous because it does not matter how powerful antivirus and security you have. After building trust the attacker can install the malware or other programs to gain control over your device/system. Also if the attack has your login credentials like user id and password then he/she can steal your online identity too.
How to stay safe from Social Engineering?

It’s a mind game of whom to trust or not on social media. The Attackers take benefits of your faith and breach the security of your system/device/identity. You can easily stop social engineering attacks with the following easy tips:
- Do not trust every person on your chat list that you have recently added. Stop yourself from sharing personal details.
- Sharing your every personal detail publicly like email id, contact no. and other details could be harmful. Put privacy on your profile so only you can see the sensitive information.
- Do not open any random attachment from a person that you have recently met.
- Always turn on the firewall on your system and look at all the antivirus warnings carefully.
- Change your password every 2-3 months later and never use the same password everywhere.
XSS(Cross-Site Scripting) Attack
[ps2id id=’8′ target=”/]
Cross-Site Scripting looks the same as the SQL injection attack but the procedure is different here. Where in the SQL injection, hacker attacks on the database of a website. In XSS, the attacker injects the malicious code/script into the database. So whenever the website launches on a victim device the attacker can control it. With Cross-Site Scripting an attacker can steal your session and perform session hijacking easily.
How hackers perform an XSS attack?
To perform an XSS attack, an attacker has to find a vulnerable website. After that, he/she inserts the script into the database using the comment section. Now every time a user requests for the web page, the script will launch automatically and the hacker can steal all the data that a user is sharing with the website. Also, the attacker can control your system, take a screenshot of your system, and discover and collect network information.
How to prevent an XSS attack on your website?

You can easily prevent any Cross-Site Scripting attack on your website if you follow this simple set of tips.
- You should use validation code to confirm that a user is only entering the simple text, not a code.
- Encrypt your website permalink for better protection.
- You can give your users an option to disable the client-side script.
Password Attack
Everybody knows that a password is a key to access an account. If someone knows your password then they can breach the security easily without facing any difficulty. That’s why most hackers target your password so they can access your account and steal your data. Social Engineering, Password guessing is some of the time-consuming types of cyberattacks. But for fast password Password Attack, there are some other tactics that attackers use.
- Brute Force: In this cyber attack, an attacker guesses the victim’s password according to his profession, personal life, hobbies, and some others.
- Dictionary Attack: You might get a warning to make passwords strong while creating an account on Facebook or Google. Because easy passwords are easier to guess and don’t give full security.
Hackers have a list of common/uncommon passwords that they use against you to log in to your account.
How to prevent password attack or brute force password attack?

Preventing a password attack is not a big deal, because the attacker targets your thinking and try to guess the password using different tactics like brute force. You have just to make a password that looks impossible to guess anyone. Here are some ways by which you can protect yourself from being attacked by a brute force password and dictionary attack.
- Some people use “Password” as their password or their contact no. And most hackers try to input the same things to breach into your account.
- Make a password that is alphanumeric means it contains alphabets and numbers. Also, make a combo of small and capitalized letters, and don’t forget to use special characters.
- Never use a password that was already breached earlier. You maybe be thinking that the Attacker might not use the same password. But that’s the big mistake you are doing. Your old password already becomes a part of a dictionary attack and if you entering the same password now then you are inviting a hacker to attack again.
- There’s an online website where you can check your password security level. Click Here to find how much time it will take to hack your password by a professional hacker.
Conclusion
As different types of cyber-attacks exist, there are also some ways to protect yourself from being attacked. There’s no two-way talk that your security is always on your hand. You can easily prevent 99% of cyber-attacks if you have proper knowledge about how they are performed. In this article, we got to know about some common classes of cyberattacks that mostly hackers perform on victims.
Which cyberattack type you find most terrific and not easy to prevent on the above list? Comment your opinion to get more security tips.














